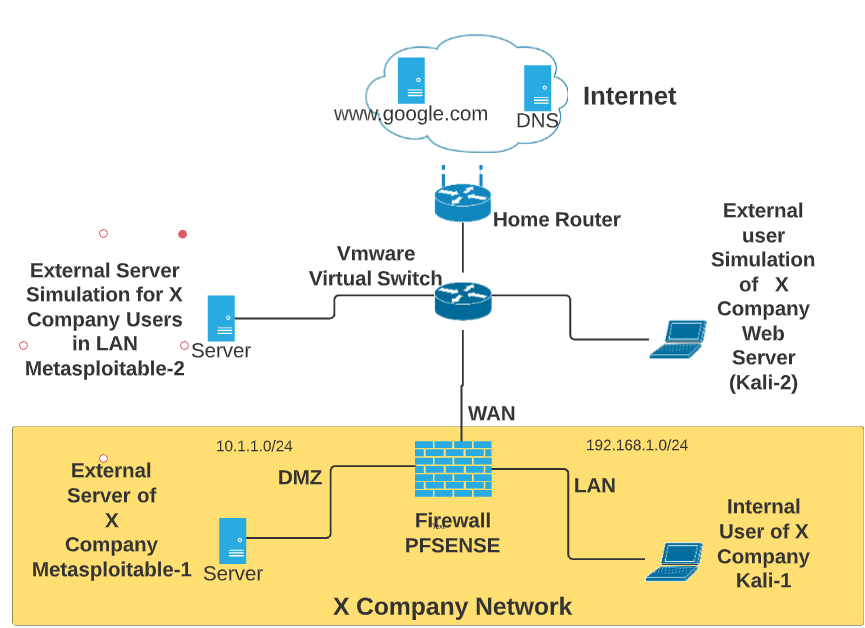
Lab 5 Penetration Testing A Pfsense Firewall . Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Make a screen capture showing a. Conduct a port scan on the network. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Which is not part of the attacker kill chain? Make a screen capture showing the results of the traceroute command. What does an effective penetration test consist of?
from ibrahimakkdag.medium.com
Conduct a port scan on the network. penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. What does an effective penetration test consist of? Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Make a screen capture showing the results of the traceroute command. Make a screen capture showing a. Which is not part of the attacker kill chain? Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver.
Firewall Practices with “PfSense” on Your Virtual Home Network Lab by
Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing a. Make a screen capture showing a. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Conduct a port scan on the network. What does an effective penetration test consist of? penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Which is not part of the attacker kill chain? Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing the results of the traceroute command.
From getlabsdone.com
pfSense GetLabsDone Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing a. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing the results of the traceroute command. What does an effective penetration test consist of? Conduct a port scan on the network. Challenge exercise in the pfsense firewall, create new. Lab 5 Penetration Testing A Pfsense Firewall.
From www.youtube.com
ISSC 421 Lab 03 Configuring a pfSense Firewall Part II YouTube Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing a. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing the results of the traceroute command. penetration testing is crucial to do, because it can. Lab 5 Penetration Testing A Pfsense Firewall.
From getlabsdone.com
How To Install Pfsense Firewall On GNS3? GetLabsDone Lab 5 Penetration Testing A Pfsense Firewall Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing the results of the traceroute command. Conduct a port scan on the network. Which is not part of the attacker kill chain? What does an effective penetration test consist of? Make a screen capture showing. Lab 5 Penetration Testing A Pfsense Firewall.
From okgo.net
Firewall Practices with “PfSense” on Your Virtual Home Network Lab Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing the results of the traceroute command. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing a. Which is not part of the attacker kill chain? What does an effective penetration test consist of? Challenge exercise in the pfsense firewall,. Lab 5 Penetration Testing A Pfsense Firewall.
From securityzone.vn
[Lab pfsense] Cấu hình NAT trên Pfsense Lab Network System Security Lab 5 Penetration Testing A Pfsense Firewall What does an effective penetration test consist of? Make a screen capture showing the results of the traceroute command. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Conduct a port scan on the network. Which. Lab 5 Penetration Testing A Pfsense Firewall.
From thuanbui.me
pfSense Lab Thuận Bùi Blog Lab 5 Penetration Testing A Pfsense Firewall Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Which is not part of the attacker kill chain? Make a screen capture showing the results of the traceroute command. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing a. Conduct. Lab 5 Penetration Testing A Pfsense Firewall.
From itspyworld.blogspot.com
Deploy pfSense VMware stepbystep Lab 5 Penetration Testing A Pfsense Firewall Which is not part of the attacker kill chain? Make a screen capture showing the results of the traceroute command. Conduct a port scan on the network. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing a. What does an effective penetration test consist. Lab 5 Penetration Testing A Pfsense Firewall.
From blog.certcube.com
Defensive Lab Series PFSense Configuration Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing a. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Make a screen capture showing the results of the traceroute command. Which is not part of the attacker kill chain? Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Conduct. Lab 5 Penetration Testing A Pfsense Firewall.
From domalab.com
pfSense Firewall rules for VMware homelab quick overview » domalab Lab 5 Penetration Testing A Pfsense Firewall penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Which is not part of the attacker kill chain? Conduct a port scan on the network. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns. Lab 5 Penetration Testing A Pfsense Firewall.
From www.vrogue.co
Building An Infosec It Home Lab 3 Configure Pfsense F vrogue.co Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing a. What does an effective penetration test consist of? penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Conduct a port scan on the network. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Which. Lab 5 Penetration Testing A Pfsense Firewall.
From www.studypool.com
SOLUTION Testing a pfSense Firewall Worksheet Studypool Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing the results of the traceroute command. Which is not part of the attacker kill chain? penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Conduct a port scan on the network. What does an effective penetration test consist of?. Lab 5 Penetration Testing A Pfsense Firewall.
From ibrahimakkdag.medium.com
Firewall Practices with “PfSense” on Your Virtual Home Network Lab by Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing the results of the traceroute command. penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Which is not part of the attacker kill chain? Configure and. Lab 5 Penetration Testing A Pfsense Firewall.
From reatfiphosiv.weebly.com
Raspberrypifirewallpfsense Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing a. What does an effective penetration test consist of? Make a screen capture showing the results of the traceroute command. Which is not part of the attacker kill chain? Conduct a port scan on the network. penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks. Lab 5 Penetration Testing A Pfsense Firewall.
From www.jsinfosec.com
Setting Up A Pentest Lab with Firewall in Virtual box JSinfosec Lab 5 Penetration Testing A Pfsense Firewall Which is not part of the attacker kill chain? Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Make a screen capture showing the results of the traceroute command. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Conduct a port scan on the network.. Lab 5 Penetration Testing A Pfsense Firewall.
From rodrigolira.eti.br
Lab pfSense Parte 01 Rodrigo Lira Lab 5 Penetration Testing A Pfsense Firewall Make a screen capture showing the results of the traceroute command. Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. Conduct a port scan on the network. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. penetration testing is crucial to do, because it. Lab 5 Penetration Testing A Pfsense Firewall.
From securityzone.vn
[Lab pfsense] Cấu hình NAT trên Pfsense Lab Network System Security Lab 5 Penetration Testing A Pfsense Firewall Which is not part of the attacker kill chain? Conduct a port scan on the network. penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Make a screen capture showing the. Lab 5 Penetration Testing A Pfsense Firewall.
From www.jsinfosec.com
Setting Up A Pentest Lab with Firewall in Virtual box JSinfosec Lab 5 Penetration Testing A Pfsense Firewall Conduct a port scan on the network. Make a screen capture showing the results of the traceroute command. Which is not part of the attacker kill chain? Configure and test split dns on pfsense make a screen capture showing your host override entries in the dns resolver. What does an effective penetration test consist of? penetration testing is crucial. Lab 5 Penetration Testing A Pfsense Firewall.
From okgo.net
Firewall Practices with “PfSense” on Your Virtual Home Network Lab Lab 5 Penetration Testing A Pfsense Firewall penetration testing is crucial to do, because it can finds vulnerabilities that exists on the systems or networks that attackers can use, so we. Make a screen capture showing the results of the traceroute command. Make a screen capture showing a. Challenge exercise in the pfsense firewall, create new inbound rules to specifically deny. Which is not part of. Lab 5 Penetration Testing A Pfsense Firewall.